Protecting Your Online Accounts: Best Practices for Enhanced Security
Introduction
In today's digital age, where our lives are increasingly intertwined with the online world, ensuring the security of our personal and financial information is of paramount importance. With the rise of cyber threats and hacking attempts, it is crucial to implement robust measures to protect our online accounts. In this comprehensive guide, we will outline the best practices for enhancing the security of your online accounts, empowering you to safeguard your valuable data effectively.
Table of Contents
- Understanding the Importance of Online Account Security
- Creating Strong and Unique Passwords
- Enabling Two-Factor Authentication (2FA)
- Keeping Your Software and Devices Up-to-Date
- Being Wary of Phishing Attempts
- Utilizing Virtual Private Networks (VPNs)
- Regularly Monitoring Your Online Accounts
- Securely Storing and Managing Your Passwords
- Conclusion
1. Understanding the Importance of Online Account Security
In an era where a significant portion of our daily activities occurs online, ensuring the security of our accounts is paramount. Cybercriminals constantly seek ways to gain unauthorized access to personal and financial information, making it crucial to adopt proactive security measures. By following the best practices outlined in this guide, you can significantly minimize the risk of falling victim to cyberattacks and protect your online accounts effectively.
2. Creating Strong and Unique Passwords
One of the fundamental pillars of online security is the creation of strong and unique passwords for each of your online accounts. A strong password typically consists of a combination of uppercase and lowercase letters, numbers, and special characters. Avoid using easily guessable information such as your name, birthdate, or common words in your passwords. Additionally, refrain from reusing passwords across multiple accounts, as this can significantly increase your vulnerability to hacking attempts.
To simplify the management of your passwords, consider using a reputable password manager tool. These tools generate complex passwords, store them securely, and automatically fill them in when needed, eliminating the need to remember numerous passwords across different platforms.
3. Enabling Two-Factor Authentication (2FA)
Two-factor authentication (2FA) provides an additional layer of security for your online accounts. By enabling 2FA, you introduce a second verification step beyond just entering your password. This often involves a unique code sent to your mobile device or generated by an authenticator app. Even if an attacker manages to obtain your password, they would still require the secondary authentication method to gain access to your account. Enable 2FA whenever possible to bolster the security of your online accounts.
4. Keeping Your Software and Devices Up-to-Date
Regularly updating your software and devices is crucial to maintaining a secure online environment. Software updates often include security patches that address vulnerabilities discovered by developers or security researchers. By keeping your operating system, web browsers, and applications up-to-date, you ensure that any known security weaknesses are patched, reducing the likelihood of exploitation by hackers.
5. Being Wary of Phishing Attempts
Phishing attacks remain a prevalent method used by cybercriminals to trick unsuspecting individuals into revealing their sensitive information. These attacks often involve deceptive emails, messages, or websites that mimic legitimate organizations. To protect yourself, exercise caution when opening emails or clicking on links from unknown sources. Verify the authenticity of websites before entering personal information, and be wary of requests for sensitive data via email or messages. When in doubt, contact the organization directly through verified channels to confirm the legitimacy of any requests.
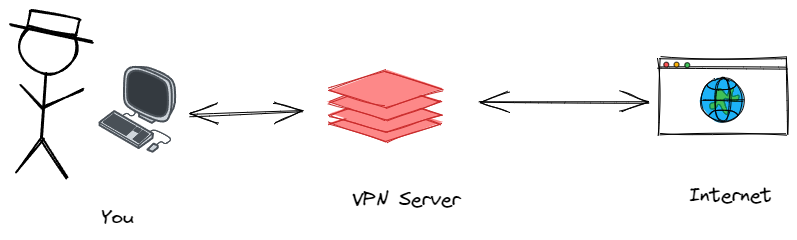
6. Utilizing Virtual Private Networks (VPNs)
Virtual Private Networks (VPNs) provide an additional layer of security by encrypting your internet connection and masking your IP address. By routing your internet traffic through a secure server, VPNs make it significantly harder for hackers to intercept and access your data. VPNs are particularly useful when connecting to public Wi-Fi networks, as these are often prime targets for cybercriminals. Invest in a reputable VPN service to safeguard your online activities and protect your sensitive information from prying eyes.
7. Regularly Monitoring Your Online Accounts
Vigilant monitoring of your online accounts is crucial for detecting any suspicious activity promptly. Regularly review your account activity and transaction history to identify any unauthorized access or unfamiliar transactions. If you notice any suspicious or fraudulent activity, report it to the respective platform or financial institution immediately. Prompt action can minimize the potential damage caused by unauthorized access to your accounts.
8. Securely Storing and Managing Your Passwords
While using strong and unique passwords is essential, securely storing and managing them is equally crucial. Avoid writing down passwords on paper or storing them in easily accessible digital formats, such as unencrypted text files. Instead, consider using a reputable password manager that encrypts your passwords and requires a master password for access. This ensures that your passwords are protected and easily accessible only to you.
Conclusion
Protecting your online accounts is an ongoing process that requires vigilance and adherence to best practices. By implementing strong and unique passwords, enabling two-factor authentication, keeping your software up-to-date, being cautious of phishing attempts, utilizing virtual private networks, regularly monitoring your accounts, and securely managing your passwords, you significantly enhance the security of your online presence. Stay proactive, stay informed, and prioritize the protection of your valuable personal and financial information in the digital landscape.
More Articles
Comments
your_ip_is_blacklisted_by sbl.spamhaus.org